Snapshot of Current Cyber Attacks on Alyne
Even though Alyne is a relatively small organisation, we are subject to a surprisingly large range of targeted phishing attacks. Our customers trust highly sensitive data for processing in Alyne and it is our responsibility to be good custodians of that data – and trust.
For everyone at Alyne that means staying vigilant and making sure we are aware of these attempts. One way of keeping awareness high is to make unsuccessful phishing attempts public so others can see what these attacks look like and avoid safely in future.
I would like to showcase some of the attempts over the past few months in the following post.
Methods
In this post I am only analysing phishing attempts through email. While our app endpoint is of course exposed to the internet and therefore subject to many attacks, the security architecture – especially our CDN and minimised attack surface prevent these from being an issue.
- Phishing links
The most basic attempts try to get the user to click on a link that is masked with more or less skill. - Links to Cloud services
One of the methods that is most worrying for me is the usage of cloud services – that an organisation might be actually utilising – to send out fraudulent emails. - Pure social engineering
The classic social engineering approach is to pose as a member of the organisation to start a line of communication in order to persuade someone to perform some sort of action that might unknowingly provide inappropriate access to an attacker. - Sharing of actual documents on cloud services
A new approach to actually invite users to collaborate on a cloud service document (e.g. OneDrive) where the document then contains a link to a malicious source.
Objectives
Obviously we may not know the exact objectives of each attack, but given that these attacks are mostly performed at scale, we can get a general idea of the motivations behind the initiatives.
- Cash Equivalents
The most straight forward attack is for the sake of simple cash equivalents. We entertained one attempt in order to see where the attack would lead. In this case the attacked / scammer was impersonating the CEO and trying to get a new employee to buy Google Play credit and send the retrieval codes via email. - Installing Malware
This is where traditional attacks originate – trying to install malicious code on the attacked machine in order to gain unauthorized access to the system. Malware has certainly evolved over time, with ransomware being the most prevalent type especially for this broader attack approach. - Information Scamming
Some of the attacks clearly have the objective of gaining information on the victim for the purpose of further social engineering. The ultimate goal from this may still be gaining cash equivalents or installing malware or otherwise inappropriate access.
Examples
At this point I would like to share some of the semi-targeted attacks that we have documented over the past months:
- CEO Mail Spoofing
One of our new team members Alex was sent this email – seemingly from me. The mail spoofing was so trivial that a click on the email sender revealed that the actual sender was certainly not my own email address.

- Fake Expense Reports or Bonus Payment Calculations
Interestingly in this example there was actually a file shared with my user via OneDrive. While no one actually opened the file at Alyne, I would imagine that there is some sort of link or malicious content included in the file. The lure is certainly to send something as “exciting” as bonus payments to get people to quickly click and see.
- Fake Voicemail Notifications
Again, an attempt to send something that people will urgently want to interact with – such as a missed voicemail. Some users may assume this is a new system that they didn’t know was implemented and click on the link. The personalisation of the message for “Alyne” is to be noted.

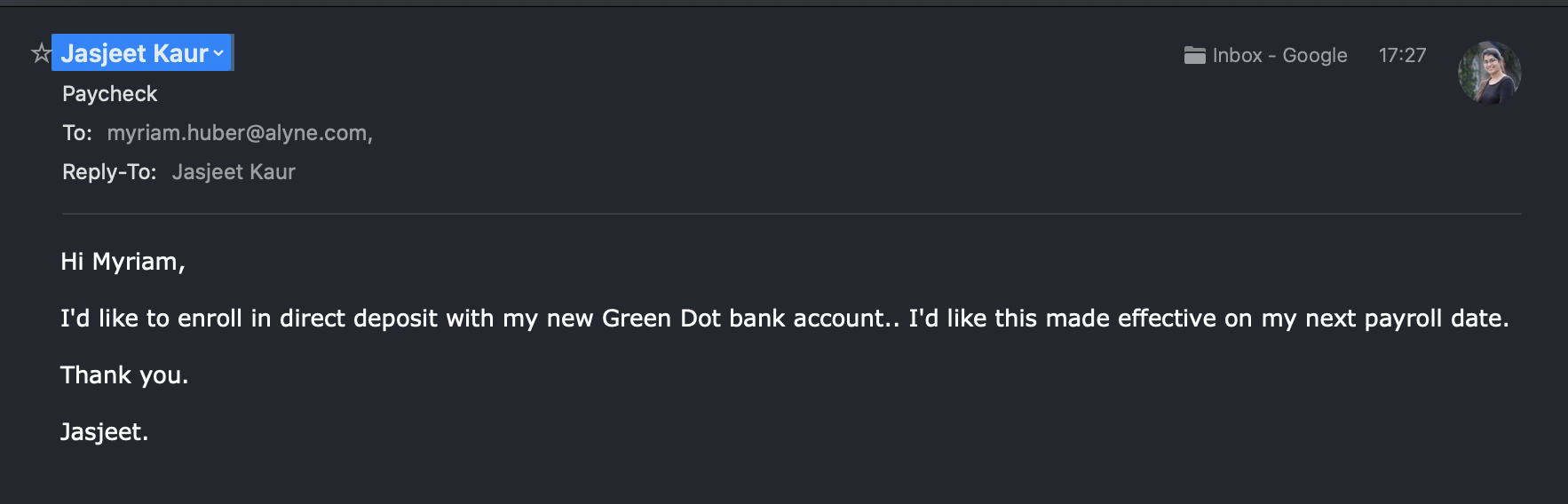
- Change of Bank Account Request
The next example is fairly targeted, as the attackers identified an employee and our Head of HR Myri and tried to have the salary account changed in HR. Myri was using Apple Mail and even though the email address was clearly spoofed, Apple Mail displayed Jasjeet’s avatar.
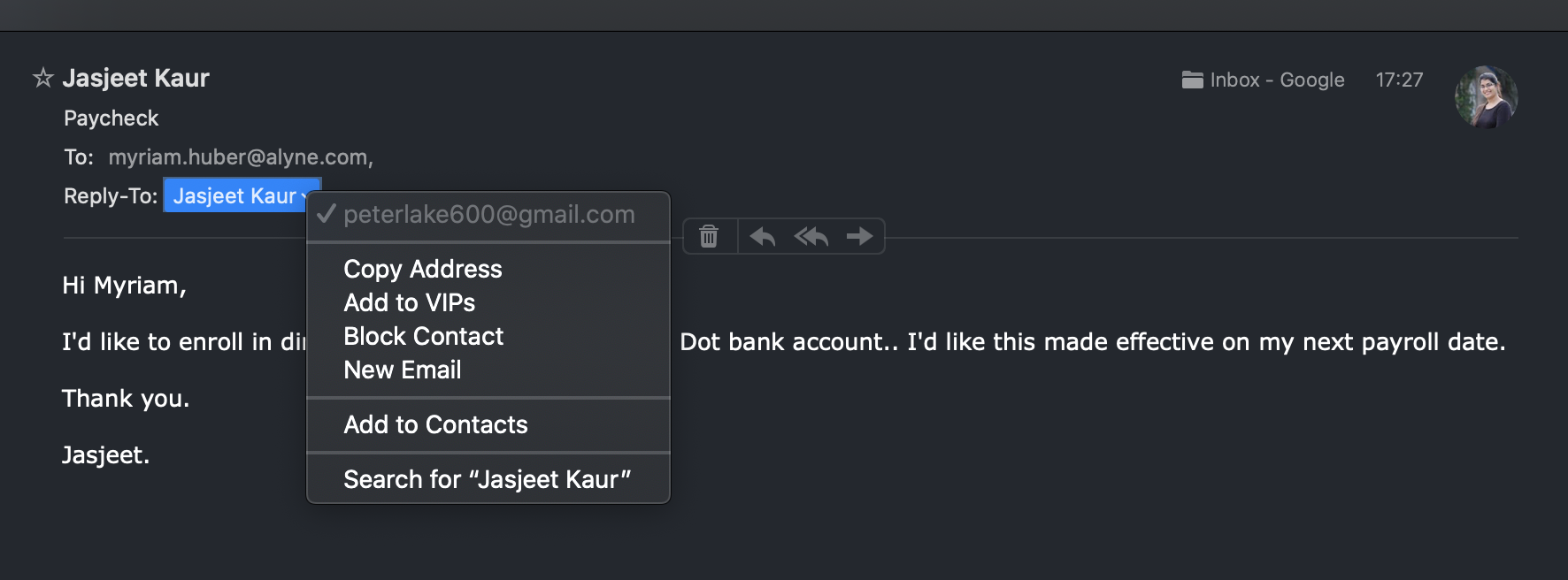
- Docusign Scam
As many businesses these days we use Docusign for signing our documents. I get quite a few of these requests for signature – sometimes invited from our Head of Legal, but also sometimes from our customers. If you are not very cautious, this mail might actually fool you.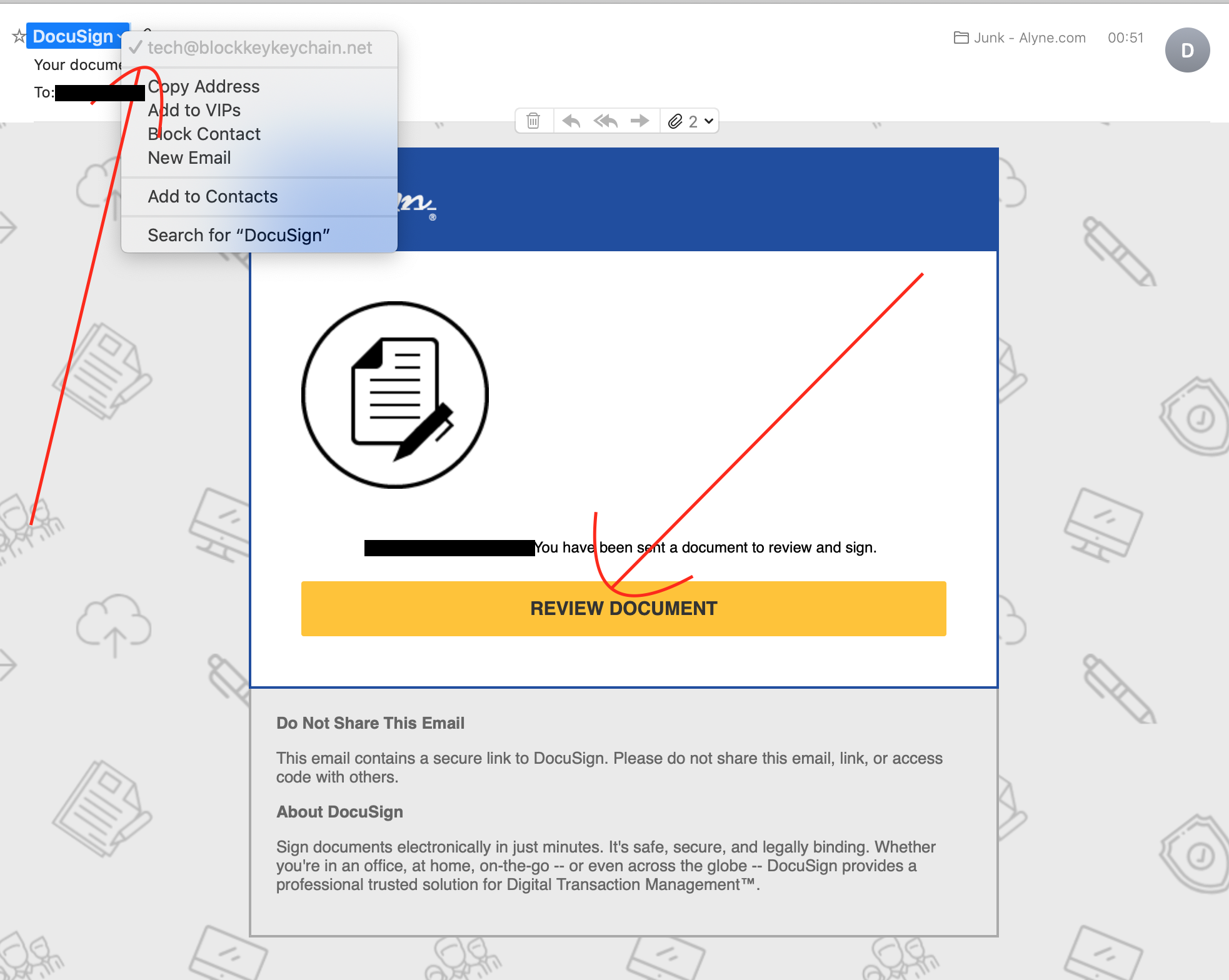
- VPN Login
Not a very sophisticated email, but very topical. With many people now working from home using a VPN, maybe access to a “new” VPN is something that could trigger them to click on this link.

- Contact Detail Phishing
Another example where the attackers identified Faris as one of our employees and the attacked tried to impersonate me in order to get Faris’ contact information. As you can see, Faris received a pretty obvious warning.
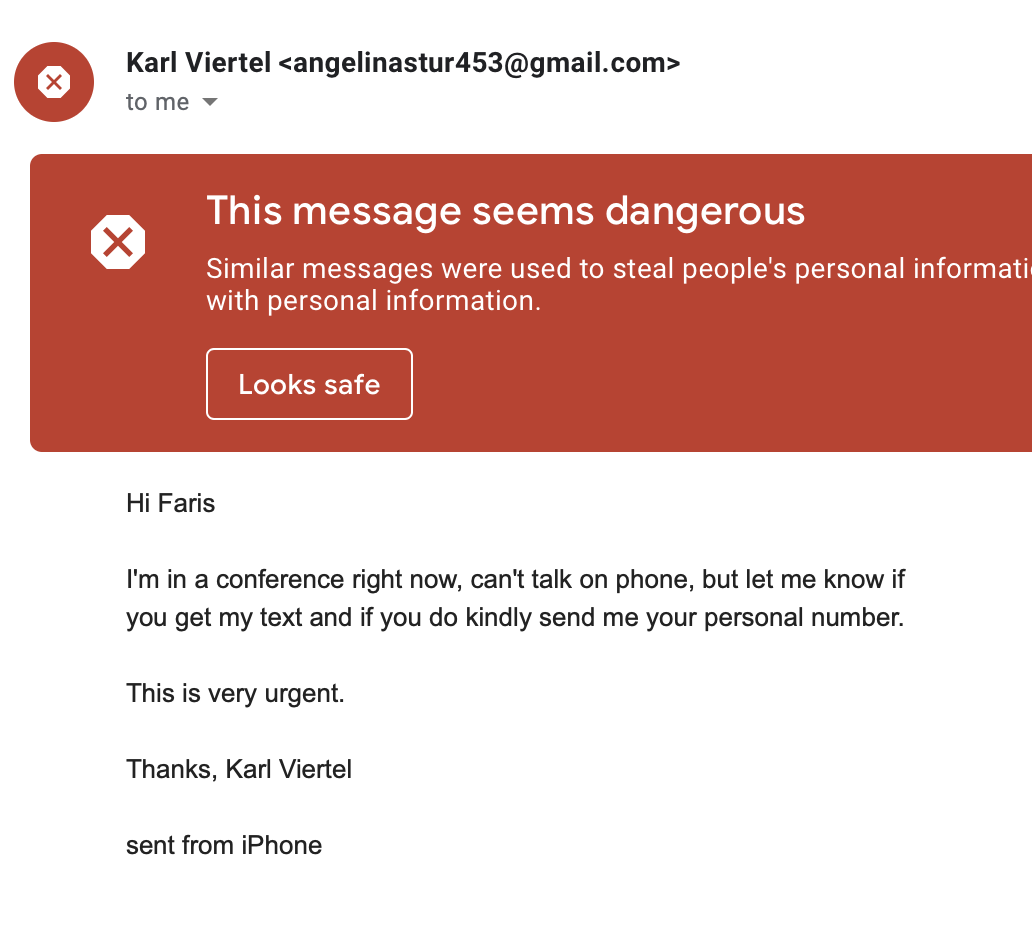
Evaluation
So what can we take away from these examples? Luckily, these attacks were not terribly sophisticated and were easy to detect. The focus or targeted nature of the attacks was slightly surprising, given we are not a huge organisation. I don’t believe all of this information can be collected 100% automated but requires some manual configuration to be executed. One very clear pattern was also targeting new joiners that may not be able to distinguish between the actual systems we use and fake phishing attacks. Generally these attacks are designed to work in big numbers with a low success rate, however the effort in configuring the attacks seems to be low enough so that it remains worth it. Using common SaaS tools (docusign, box, etc) as a scam vector shows how these attacks are evolving. Probably the smartest move was to use cloud file services to share files containing malicious content (i.e. OneDrive). This almost guarantees the email is delivered to the victim and passes through spam and malware filters undetected.
Mitigations
The most effective mitigation remains awareness within the team. We make this a topic regularly at all hands meetings, in our comms channels and during our onboarding. Keeping people sensitive to the threats of phishing is key.
At Alyne we use Google for Work and the associated email service. If you compare the interface of the “Change of Bank Account” example with the “Contact Detail Phishing” example, it is clear that using the Google Mail interface has some significant security advantages.
Finally we implore all of our employees to always perform a second channel confirmation if even the slightest of doubts exist. Our core communication platform is Slack. I tell employees that I will never ask them to do anything via email. If I ever do, always confirm on a second channel (phone, slack, in person).










