Risk never sleeps.
To help organizations stay one step ahead, Alyne’s cloud-based, AI-driven governance, risk and compliance (GRC) platform makes continuous risk monitoring and management easy with:
- A fully web-enabled & mobile-responsive design
- Dynamic dashboards & reports
- Scalable risk assessments
- Ready-to-go templates
- Intuitive navigation
- Powerful enterprise integrations
- Globally enabled, multi-language capabilities
From enterprise and third-party risk management to ESG and information governance, Alyne helps CISOs and risk professionals understand and thoroughly assess risk, confidently implement compliance requirements, leverage and report on analytics for more risk-aware decisions, and drive 24/7, agile defense against threats.
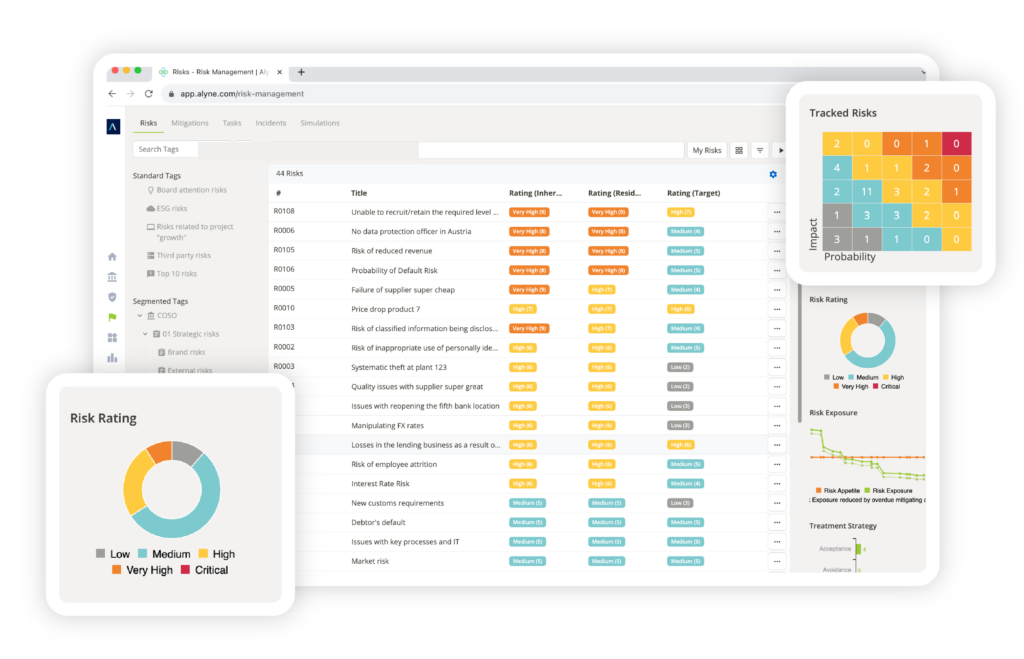
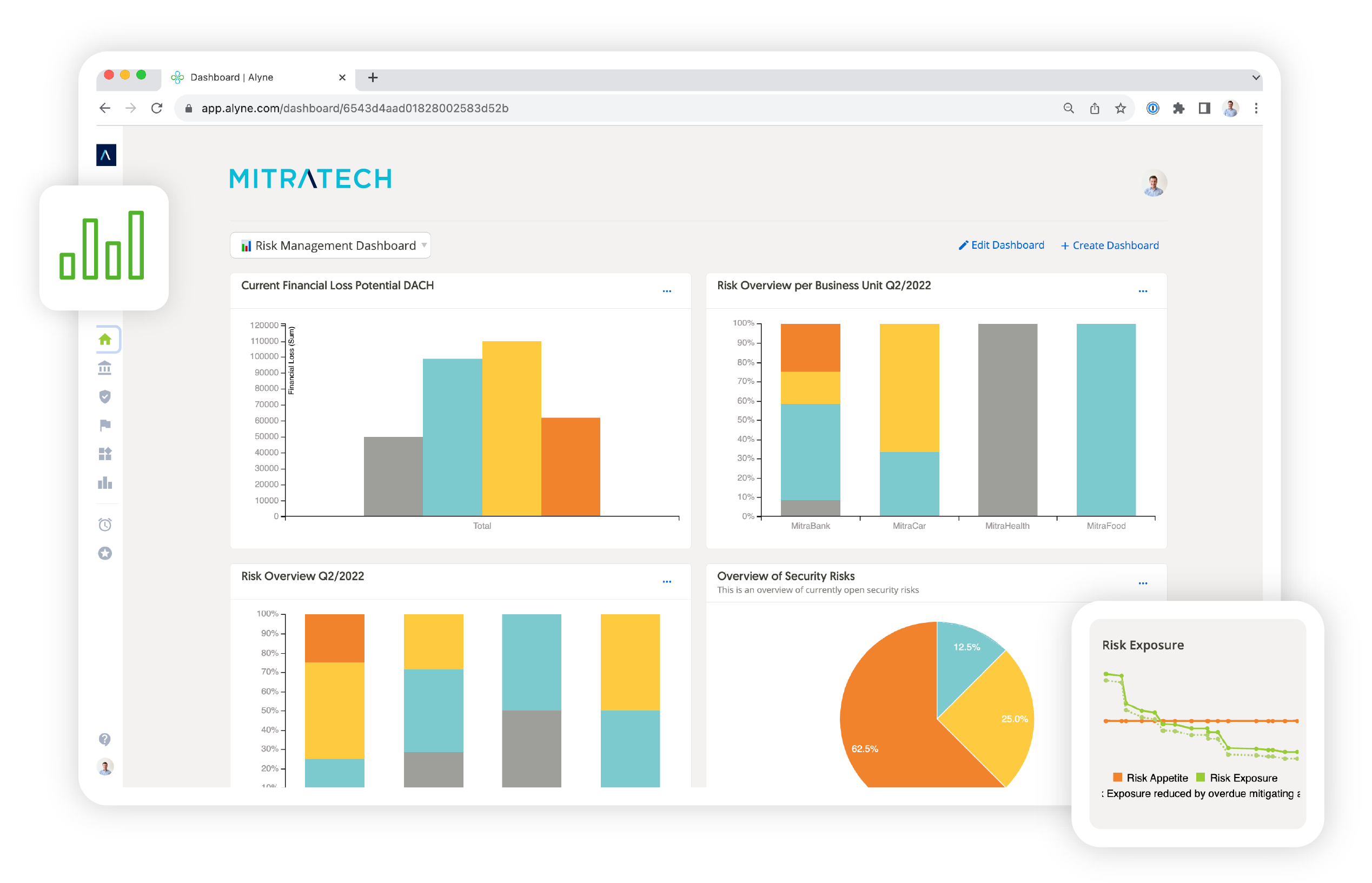
Get around-the-clock, 360-degree visibility with automated GRC platform solutions.
Alyne makes it quick and easy to get the platform up and running with workflows that stand up quickly (without any coding) and configurable dashboard capabilities to drive internal collaboration, Meanwhile, a powerful AI engine works full-time behind the scenes to:
- Streamline risk identification and qualification processes
- Automatically interpret policies and operational documents
- Quantify risks via a built-in simulation engine
- Continuously evolve to meet your regulatory compliance needs with new features like advanced document mapping, summarization capabilities, and more
The result is a real-time, 360-degree view into your organization’s risk and compliance profile along with the analytics to help you keep making the right decisions.
Ready to automate your risk management strategy and start catching every red flag?
See what you can do with Alyne.
REQUEST A DEMO
Fighting new-age risks requires a cutting-edge GRC platform:

AI & ML engine
Alyne pairs expert-trained artificial intelligence with machine learning to help users identify and understand regulations, then mitigate and report on the risks.

Real-time integrations
Integrations with 3rd-Party Data Providers such as Black Kite and SecurityScorecard, in addition to internal data sources, ensure data is always current to make accurate and informed decisions.

No-code workflows
Cut cost of ownership with no-code configuration and workflows, allowing non-technical users to customize Alyne to their needs.

1,500 out-of-the-box templates
Mitigate risk in fraction of the time by leveraging over 1,500 pre-defined templates mapped to regulations and controls.

Identification of compliance and regulatory requirements
Covering Regulations: ISO 27001, SOC 2, SS1/22 & SS2/22, COBIT, NIST, CCAR, sr 11-7, DFAST, SOX, TRIM & more.

Intuitive UI and UX
Boosts adoption and collaboration across the entire organization, and requires zero training to use.
One partner. One platform.
Everything you need to elevate your Governance, risk and compliance.
REQUEST A DEMO
Integrated GRC tools & software solutions for every use case
From Enterprise Risk Management (ERM) and Data Privacy to Policy Management and QHSE Incident Support, explore integrated GRC tools and software solutions for every need.

Third-Party Risk Management Solutions
Proactively monitor and mitigate operational third-, fourth-, and nth-party risks, boosting transparency and the ability to take swift action where necessary.

Information Governance Solutions
Better collect, store, analyze, and manage your data in line with corporate policy and regulatory requirements.

Enterprise Risk Management (ERM) Solutions
Embed risk management across your enterprise – and become everyone’s strategic partner.
“We are thrilled that just six weeks after its implementation, we were able to fully run our Risk Inventory process within Alyne, significantly reducing internal reconciliation and coordination efforts, as well as significantly increasing the transparency and quality of the risk inventory”
Frequently-Asked GRC Platform Questions
GRC (Governance, Risk, and Compliance) is the integrated collection of capabilities that enable an organization to reliably achieve objectives, address uncertainty, and act with integrity — to achieve Principled Performance.
Typical functions and operations to look for in an effective GRC platform include real-time risk assessments and mitigation, third-party risk management, policy management, information governance, protection against malware ransomware, phishing, social engineering, and more.
Some of the top benefits of GRC tools and software include improving operational efficiency, automating compliance, centralizing business-critical information, mitigating risk, and a far quicker time to value than on-premise deployment solutions.
Mitratech’s Alyne
Learn more about Alyne and how it can ease your process by requesting a demo today.




